One of the newest services made available by WatchGuard is DNSWatch. DNSWatch is a cloud-based service that can monitor outbound DNS requests and can use this to block access to malicious content. DNSWatch focuses on protecting your users against phishing domains and is not dependent on the ports that the connection is made through.
Hardware and Licensing Requirements
Available through the Total Security Suite subscription
Available to Firebox T and M Series devices, as well as the Firebox Cloud and FireboxV virtual models
Firmware Requirements
12.1.1 Firmware or higher
How DNSWatch Works
When DNSWatch is enabled on your Firebox, the Firebox is registered to the DNSWatch cloud, which is available under your account at www.watchguard.com. After the Firebox is attached to the DNSWatch cloud, it will receive the IP addresses of the two DNSWatch DNS servers that will be used to monitor outbound DNS requests.
Once applied, DNSWatch will work to determine if the outbound requests are a known threat.
If the domain is not a known threat:
DNSWatch will resolve the request to the requested destination.
If the domain is a known threat or is on the DNSWatch blacklist:
DNSWatch will resolve the domain to the IP address of the DNSWatch Blackhole Server.
The server will attempt to gather more information about the threat from the device that made the request.
For HTTP and HTTPS requests, DNSWatch will redirect the user to a customizable deny page.
Configuring DNSWatch on the Firebox
The configuration of DNSWatch is a very simple process and will only take a few minutes.
1. Ensure that the Feature Key on your firewall is up-to-date and that DNSWatch shows as licensed.
2. In Policy Manager, go to Subscription Services > DNSWatch
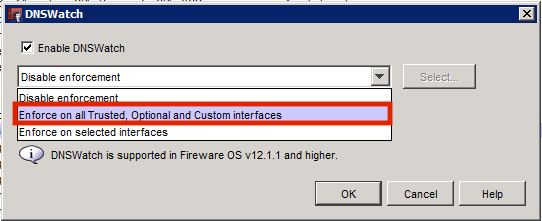
3. Check the box for Enable DNSWatch
4. Select the drop-down menu. This is where you decide which network to apply DNSWatch to. It is recommended that you select Enforce on all Trusted, Optional and Custom interfaces.
If you would like to select the specific interfaces to apply this to, select Enforce on selected interfaces, and then hit the Select button. This will allow you to manually specify the interfaces you would like DNSWatch applied to.
5. Save the policy to your firewall.
PLEASE NOTE: No changes need to be made to the DNS settings on the firewall for this service to work.
The DNSWatch Cloud
In order to monitor and make changes to DNSWatch, log into your account at www.watchguard.com. Once logged in, go to My WatchGuard > Manage DNSWatch.
The first portal that opens will show you general DNS activity. From here you can monitor DNS connections by time frame, and can see the top-visited domains.
If you click on View Reports on the first page, this will take you in to see further detail and breakdown on the DNS traffic that has been accessed from your network.
Under Domains > Blackholed, you can manually enter domains you would like to block.
Under Domains > Whitelisted, you can manually enter domains that will never be denied by DNSWatch.
User Training
One of the key features of DNSWatch is that it implements anti-phishing training for your users. If a user accesses a site that is blocked by DNSWatch, they will find themselves at a portal with a training video.
This portal can be edited to better suit your organization. To access the edit function, click on your login name in the upper-right, and then click Settings. You will see the options on the left to edit both the content and style of the deny page.
DNSWatch vs. WebBlocker
One of the biggest questions that comes up when discussing DNSWatch is why it is necessary if you have WebBlocker content filtering. The answer comes down to the job that each performs.
With WebBlocker, you are blocking access to websites based off of their categorization. These sites are not necessarily malicious, just deemed inappropriate for your work environment. Let’s take social media sites as an example. You may decide as an organization that you do not want to allow employees access to these sites for productivity reasons. If we were relying on just DNSWatch, these sites wouldn’t be blocked because they do not (typically) contain malicious content. Therefore, we would block them through WebBlocker.
As the reverse of that, WebBlocker cannot always identify a malicious site. There are security-related categories that can be selected, however a site that is found to be malicious may not get recategorized immediately. In that case, just relying on WebBlocker would leave your environment prone to threats. For this, we rely on DNSWatch.
The important thing to understand when discussing the two services is that one is not replacing the other. WebBlocker is still important in regards to determining the actual content that users are allowed access to. DNSWatch is designed to stop them from accessing malicious sites, no matter the category.